Digital identity has advanced over time, most recently culminating in self-sovereign identity (SSI). In this Trinsic Basics post, we are going to briefly cover the different models of digital identity and how SSI is the next step in the digital identity evolution. The content in this post is inspired by a blog post written by digital identity expert Timothy Ruff in 2018.
Model #1: Siloed identity
The first model of digital identity is the siloed model, and its name describes exactly how it works. In the siloed approach, in order to interact with another company or institution digitally, you must open an account, typically with a username and password. Through this process, the company becomes your identity provider. Over time, you’ll end up managing hundreds of accounts from hundreds of identity providers.
Your identity provider stores your username and password and other personal data in large data silos. In other words, your personal data is stored with all of the other customers’ personal data in one central location controlled by the company.
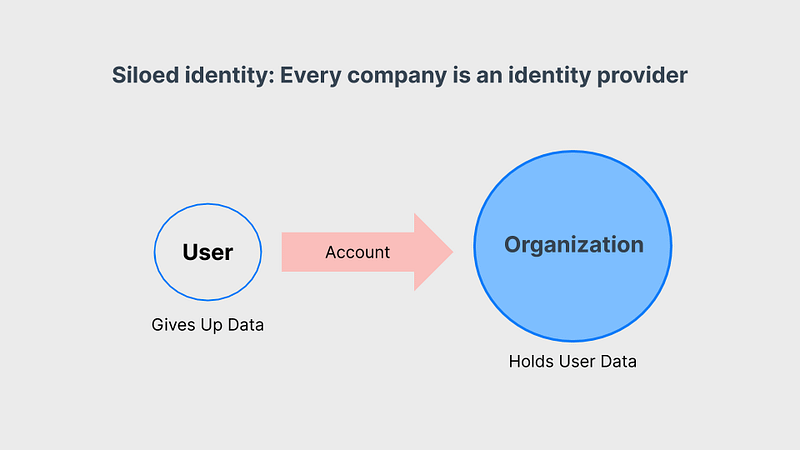
The siloed model is broken because it is:
- Centralized. You are not in control of your digital identity—the company or institution is. If they choose to block your account or if they shut their doors, your account, along with all of your data, would be gone.
- Not secure. Data silos are gold mines for hackers since they essentially only have to crack one silo to gain access to the personal data of a lot of people. Besides this, account security usually relies on a username and password, and research shows that people do not typically create secure passwords and often use the same username and password for many of their accounts.
- Poor user experience: How many times have you forgotten your password and had to recreate it? Having so many different accounts with (supposedly) unique usernames and passwords has led to a frustrating customer experience when trying to access services digitally.
Model #2: Federated identity
Digital identity advocates saw the flaws of siloed identity and sought to create a more user-centric approach.
Instead of every company needing to be its own identity provider, anyone could be an identity provider! You could, theoretically, be your own identity provider! But ultimately, this approach to “federated identity” was taken over by big tech companies.
Although we may not be familiar with the term, we are all very familiar with how federated identity works. The most common federated identity example is the “Login with Google” or “Login with Facebook.” With federated identity, large tech monoliths act as middlemen between you and the company you are interacting with digitally. Instead of the company managing your identity data, the middlemen do.

Although the federated identity model improves the user experience, it too suffers from some problems:
- Reliance: In this model, technology monoliths provide us a digital existence. Instead of being independent and in control, we subject ourselves to the whims of the middleman. This has led to anti-trust and anti-competitive behavior that is problematic.
- Universality: Logging in with Facebook might work for buying shoes or signing up for a newsletter. But business tools, regulated industries (financial, healthcare, government), and privacy-focused industries will never accept your personal social media account as authentication because it has almost no assurance—anyone can create multiple Google accounts with ease.
- Surveillance: When you login with Facebook, Google, or some other service, you give that middleman more data points they can use to track and spy on you so that they can increase their revenue. Interests are fundamentally not aligned between people and the middleman.
Model #3: Self-sovereign identity
Various approaches have been tried over the years to put individuals in more control of their identity, but they’ve struggled to get adopted. Finally, self-sovereign identity appears to be the solution.
Various technical innovations including blockchain, verifiable credentials, digital wallets, DIDs, and more gave rise to a new, decentralized identity that not only improves the user experience but also the security of the internet. SSI can be summed up as a movement that claims digital identity should be just as legitimate and nuanced as a person’s human identity, while being accessible to all, privacy-preserving, and not reliant on a single government or corporation.

With SSI, you’re your own identity provider because, as an individual, you have a human identity! Nobody gave you your real-world identity, so likewise, you don’t need someone to give you a digital one. Instead, you control the information that makes up your identity information as well with whom you share that information with. For the first time ever online, SSI makes it so that you interact as a “peer” with other people, organizations, and more.
Trinsic is the easiest way to implement SSI
At Trinsic, we are trying to make this third model of digital identity a reality. Our company’s mission is to make the world and its services more accessible by making self-sovereign identity more accessible. We’ve done that by creating the world’s most advanced SSI platform. Experience SSI firsthand by creating a free Trinsic Studio account today. For a deeper explanation of SSI, check out this blog post.