“Identifiers” are how you are identified as a unique person and recognized as that same unique person over time. With other people, your primary identifier is your face. With organizations, it might be a student ID, social security number, or driver’s license number. Online, it might be a username, phone number, or email address.
Using identifiers properly helps to avoid confusing two people with one another. But identifiers can also be harmful—if a hacker gets ahold of your social security number, it could mean trouble!
Most identifiers are given to us by centralized registration authorities like governments, telephone companies, and email providers. But that puts an organization in between us and our ability to access basic services, compromising privacy and putting individuals in a position of powerlessness. The answer to this problem is a W3C standard called Decentralized Identifiers (DIDs).
A new type of identifier
DIDs are “a new type of globally unique identifier”¹ that is used in self-sovereign identity (SSI). It looks like this:
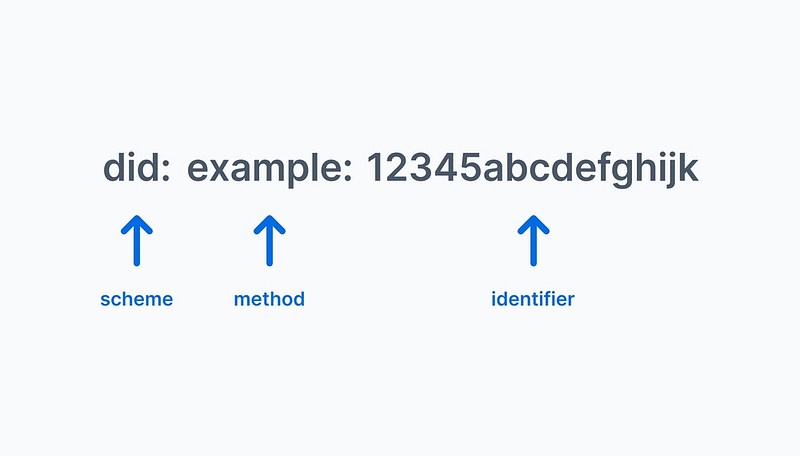
You’ll notice it has three parts:
- Scheme: DIDs all start with
did:just like how all website addresses start withhttp://. This is so that computers can tell what they’re looking at. - Method: After DIDs are generated, they have to be stored somewhere. They’re often stored in a blockchain or a digital wallet, but they can be stored anywhere. The method, which is the
example:part of the DID in the example above, tells computers where to go to find the DID. For example, issuers of verifiable credentials in the Trinsic platform get a DID that has adid:key:method, because the DID uses Static Cryptographic Key pair. - Identifier: This is the unique identifier of the DID.
According to the W3C, a DID has the following four characteristics²:
- Decentralized: There should be no central issuing agency. That means you should be able to create your own DIDs independently of anyone else.
- Persistent: The identifier should be inherently persistent, not requiring the continued operation of an underling organization. This is in contrast to your email, for example; if Gmail shuts down, you’d lose access to your Gmail messages.
- Crytopgraphically verifiable: It should be possible to prove control of the identifier cryptographically.
- Resolvable: It should be possible to discover metadata about the identifier.
How are DIDs used?
As identifiers in the Trinsic system, DIDs serve two primary functions:
- Publicly identifying credential issuers
- Privately identifying relationships (connections)
Credential issuers need to be publicly identifiable if they want the credentials they issue to be verifiable. We use a blockchain to post the issuers’ DID, which acts as a public key. The issuer signs the credential attributes with the corresponding private key.
Each relationship in the Trinsic system is called a connection. When you make a connection, you create a DID just for that relationship and share it with the counterparty. When you want to send messages, you encrypt them so that only the counterparty can decrypt the message using the DID you shared with them. This creates a super secure, peer-to-peer channel to interact. The identifiers for these connections are kept privately in your (and the counterparty’s) wallet.
If you are interested in learning more about DIDs, feel free to contact us or read the W3C’s DID specification at https://www.w3.org/TR/did-core/.
Notes
- This phrase comes from https://www.w3.org/TR/did-core/.
- These four chracteristics and descriptions come straight from https://w3c.github.io/did-use-cases/.