Trinsic makes verifiable credentials and self-sovereign identity (SSI) easy for developers to implement, so it is only fair we make it easy to conceptualize as well! The term “verifiable credentials” can seem a bit technical and overwhelming at first glance. But in reality, verifiable credentials are simpler than you think.
Start with what you know
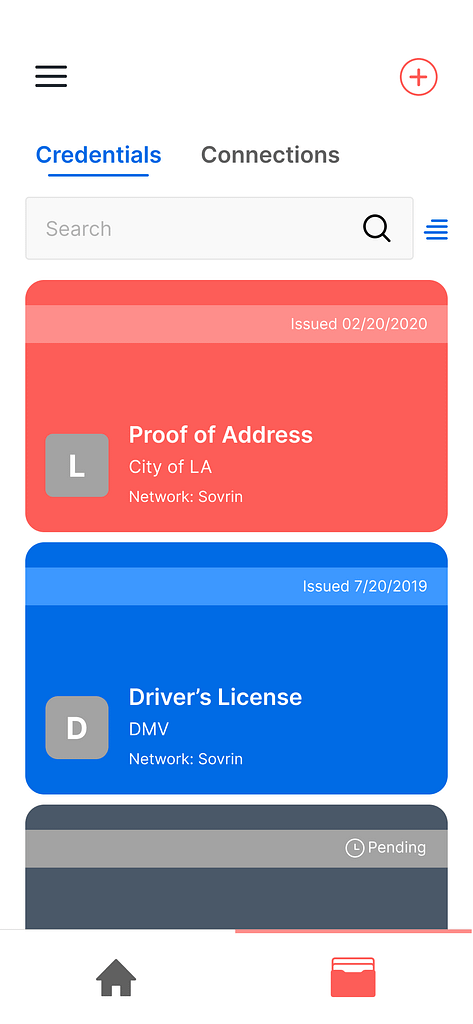
Let’s begin with the word “credential.” When we use the word credential, we are talking about any document, card, certificate, etc. that contains information about something. We use credentials every day, including driver’s licenses, passports, diplomas, insurance cards, medical test results, employee badges, and more.
All of these examples are physical, paper, or plastic credentials that you can hold in your hand. However, a credential becomes a verifiable credential once it is in a standard, digital format which you keep in your phone or the cloud. And that leads to our simple definition of verifiable credentials:
Verifiable credentials are standardized, digital certificates that make it easy to share information online in a private and secure way.
We say “standardized” because the way verifiable credentials should be built has been standardized by the internet’s leading standards body. That means there is a correct way to create a verifiable credential, and at Trinsic, we make it easy for you to do so.
The verifiable credential model
When it comes to using verifiable credentials, it important to know these three roles:
- Issuer: The issuer is the person or organization that creates the verifiable credential and gives (“issues”) it to a person, organization, or thing. (e.g., a DMV)
- Holder: The holder is the person or organization that holds the verifiable credential in their digital wallet. (e.g., a person who receives a digital driver’s license from the DMV)
- Verifier: The verifier is the person or organization that gets information shared with them. They can authenticate the information they receive instantaneously. (e.g., a security agent at the airport checking your license)
Often called the “Trust Triangle,” the image below is a classic diagram used to help conceptualize the verifiable credential model.

An important thing to note is that while the integrity of the information can be verified, the truthfulness of it cannot. So although the verifier needs to trust the source of the credential (ie., the issuer) it doesn’t need to contact the issuer directly in order to verify the information.
The unique properties
Verifiable credentials are unique from other kinds of digital documents because they are:
- Portable: With just a few clicks, you can send the credential online to anyone you please. You can also move wallets between different providers if you’d like.
- Verifiable: The reason why they are called verifiable credentials is because they allow you to verify the following things: 1) who issued the credential, 2) who the credential was issued to, 3) if the information within the credential has been tampered with, and 4) whether the credential has been revoked.
- Private: Through zero-knowledge proofs, you can pick and choose what information you want to share on a credential (you don’t have to share all of it).
- Tamperproof: Verifiable credentials can’t be altered or forged.
Trinsic's role in all of this
Trinsic is the best way to implement verifiable credentials.
- Simplicity: We make integrating verifiable credentials easy to do. Trinsic Studio removes all of the complexity of getting started, and our APIs abstract low-level protocols to help developers get going fast.
- Functionality: Trinsic Studio is an easy-to-navigate platform that has all the features you need to issue, verify, and revoke credentials.
- Scalability: Take advantage of our APIs to programmatically issue and verify millions of credentials.
- Resilience: Our platform is built on ledger-agnostic, standards-compliant, open source tech that we’ll always maintain.

Don’t take our word for it. Get started with verifiable credentials today by signing up for a free Trinsic Studio account. For more information on the pieces that make up a verifiable credential, read more on our documentation site in the Knowledge Base section.