I’ve been convinced the world needs self-sovereign identity (SSI) since my first encounter with it during an interview with Phil Windley for the first job opening at Sovrin Foundation. With fraud, deep fakes, and data breaches abounding, my belief has only expanded; so much so that I, together with cofounders, started Trinsic to make SSI easy to use. When we began 18 months ago, the tools SSI-interested businesses had at their disposal were dreadfully far from usable. After we launched the first production-grade verifiable credential platform, we’ve become the first choice for over 1,000 developers and businesses around the world.
Since technology stopped being a blocker for SSI adoption (seriously, you can issue credentials in production in less than five minutes using Trinsic Ecosystems), hundreds of teams began building solutions. But now all of these teams have a new challenge (this shouldn’t surprise you): SSI is most valuable when it’s widely adopted. Like other standards, SSI benefits greatly from a network effect which forms as adoption grows. The immediate business value of SSI at a given point in time is an exponential function of the state of adoption.
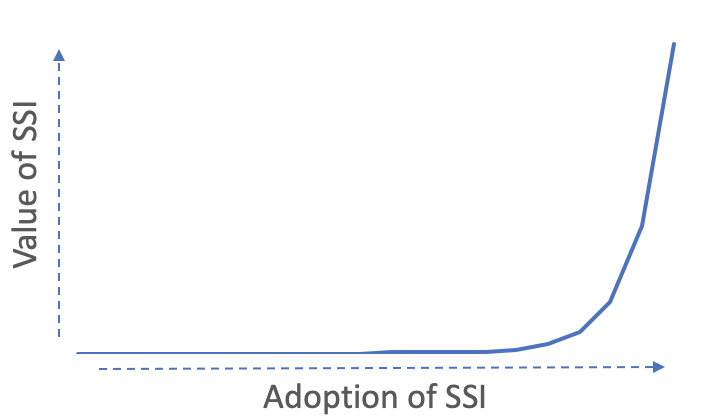
The crux of the matter therefore is: Many implementers won’t realize the potential of SSI until it’s deployed at scale, but in order to get to scale, we need implementers to realize value. It’s the classic chicken & egg problem.
For Trinsic and our customers, partners, and the broader SSI space to achieve the tremendous economic opportunity SSI represents, this adoption problem needs to be solved. We want to do our part to help the SSI space solve this problem, so I decided to interview close to 50 business leaders who are seeking to deploy SSI in production to glean their learnings. The interviewees included our “competitors” (at this stage we’re more collaborative than competitive), a few of Trinsic’s customers, and industry leaders. I have summarized and consolidated their insights and my own thoughts into 4 keys for SSI adoption.
Understanding timing of verifiable credential adoption
The first key to cracking the SSI adoption challenge in your solution is to understand our current place in the verifiable credentials adoption curve; at different phases of adoption, different growth strategies should be employed. A natural metric to gauge the state of SSI adoption is the number of verifiable credentials deployed in production. (My definition of “production” for the purpose of this piece is that a credential is 1. issued, 2. accepted by someone/something, 3. to solve a real problem that results in 4. the creation of real business value¹.)
At the beginning of 2020, I estimated there were only a few hundred verifiable credentials in production. As of October 2020, based on my interviews with all major vendors and many business leaders, I estimate there were the following number of credentials in production:
56,115 verifiable credentials in production
Given the billions of credentials I believe will eventually exist, one could easily argue that 56,115² is little more than a drop in the ocean. On the other hand, while the websites created pre-1995 easily fit on a Wikipedia page, they represented the important start of an enormous flywheel. The growth of the SSI market from ~a few hundred to ~56,115 production verifiable credentials in only 10 months is a strong signal of a market that is growing fast.
During my interviews, I also asked everyone their opinion on when verifiable credentials will really “take off”. New technologies always have a long, slow ramp-up, growing linearly until they hit an inflection point where their growth becomes exponential. It’s impossible to predict when this inflection point will occur, but according to my interviews, experts believe it will be as soon as three years away, but not longer than five years away.

It’s important to understand where we’re at in the adoption lifecycle so that you can spend your time focused on the right things. It may be too early for point-of-sale systems integrations, but the perfect time for an SSI-powered loyalty program. Given that most experts believe we’re still a few years away from mainstream adoption of SSI, should you want to build a verifiable credential-powered business? Maybe. Would you rather have started an internet company in 1996 or 2001? The earlier you build, the more upside potential exists. But I believe, like the internet, there will be business opportunities in this space for decades to come.
Selling the value of SSI
The next key to adoption is to sell the value. Verifiable credentials unlock different kinds of value for different players in an ecosystem. Sometimes it’s the issuer who benefits from issuing the credential, while other times it’s the verifier that consumes the value. The business case for verifiable credentials is different for each use case, but here are some tips that apply regardless of the business model.
- Don’t sell the tech; sell the solution to a problem
People spend money on solutions to problems, not on technology. (I don’t buy pharmaceuticals—I buy relief from my heartburn.) When you’re selling your solution, don’t lead with the technology. The technology discussion is best-suited as a “nail in the coffin” after the business value is clear.
A commonality across all production use cases is that they start small. Pick an initial, clear, quantifiable benefit to the customer and build for that. For example, although verifiable credentials offer the ideal platform upon which to build an internationally-portable eKYC system for banks, perhaps it’s better to start initially with authenticating users to ATM machines. Amazon began with the vision to be the “everything store” but started out selling books. It’s ok to grow into your ultimate vision. - Don’t talk past your buyer
With a new technology like verifiable credentials, there are lots of potential reasons a buyer could be interested. Before diving in to your sales pitch, make sure you understand the problem your buyer is trying to solve and speak to that. If you’re selling instant verifiability of data and they’re wanting to buy improved, trusted communication, you’ll have a tough time.
Some enterprises are still trying to figure out their OIDC or SSO strategies, for example. If the business value you’re selling is secure authentication, the buyer might feel like they’re too premature. But if you’re selling the ability to future-proof the company’s identity-related investment, you might have better luck.
Overcoming obstacles for going to production
The third key to adoption is to overcome the obstacles that will inevitably come. All new technologies need to overcome obstacles to go to production. Most of these obstacles are common regardless of the technology, but a few are unique to verifiable credentials. My interviews consistently identified 10 distinct obstacles blocking teams from going into production. Here, I’ll share a short thought on how to mitigate them.
Which came first, the issuer or the verifier? Overcoming the chicken/egg problem.
The last key to SSI adoption is overcoming the chicken/egg problem. It’s easy to envision a future where verifiable credentials are ubiquitous and useful; everyone has a digital wallet with useful credentials issued by trusted entities which are accepted by verifiers everywhere. But until there are companies issuing verifiable credentials, why would one begin to verify them? And until there are verifiers, why would a company sign up to be an issuer of them? And until there are places to get credentials and other places to use credentials, who will download a digital wallet?
This is a classic question of causality: How does one cause a market to emerge? When I asked this question to the experts I interviewed, I was surprised at their answer.
- 50% of respondents believed an ecosystem-driven approach was the best one
- 50% of respondents believed a single-sided approach was the best one
Personally, I think both are justified, depending on the use case.
Ecosystem approach
An ecosystem-driven approach is a method to overcome the chicken-egg problem where an entity brings together all sides of the market at the same time. If we take COVID-19 test results as an example, an ecosystem approach would bring together doctor’s clinics & labs (issuers), employers (verifiers), and patients (holders) all at the same time. By curating an entire ecosystem of participants, each can receive the full measure of the value they could expect when verifiable credentials are widely adopted. The challenge with this approach is bringing together all sides of the market simultaneously; it may take longer and cost more than expected. Even in this approach, the use case will need to be constrained in some way (scope, geography, etc.).
Single-sided approach
What I’ll call a “single-sided” approach, as opposed to a two-sided or three-sided marketplace, is where a single participant gets value from verifiable credentials. Using the same example, in a single-sided approach, the vendor might sell verifiable credentials only to the lab as a way to improve deliverability of test results. This adds immediate value to the lab through standard digital transformation value-adds; process automation, cost reduction, etc. It allows the vendor to focus the value proposition on a single entity instead of curating multiple.
Once an entity is already issuing credentials, it may be easier to sell a solution to the verifiers of those credentials.
Conclusion
The chart on the right illustrates the adoption of the fax machine over time. It had to overcome the chicken and egg problem at first, too. It took a long time, but ultimately it only needed two things: specific, individual “killer use cases”, and recognition as a global standard. SSI is well on its way to both.
Every trusted market in the world will be impacted by verifiable credentials. Billions of dollars of economic value will be created by this new medium for exchanging trusted data, and the early implementors building products with this technology will be rewarded handsomely. I hope these four keys help teams do just that.

Trinsic is focused on building the best tools to enable developers and other innovators to easily build with verifiable credentials. Over 1,000 developers and companies choose to build on Trinsic.
If you’re building a solution and want more support, or would like to give feedback on this work, reach out to us here.
Notes
- All four elements are important. Some interesting SSI cases don’t fit my definition but are cool nonetheless. BCGov’s OrgBook satisfies all of these except #2 (because OrgBook credentials are issued to a public registry, not a person or entity, so they don’t count in my arbitrary definition of “production”). Likewise, if you book a meeting on my calendar, you’ll get a verifiable credential confirmation in your inbox (powered by our integration partner Zapier). This satisfies all but #4; its primary purpose is demonstrative and doesn’t actually solve a real business problem.
- The other thing I’ll add is that the number of verifiable credentials in production is far from a perfect metric. For example, some groups I spoke with had issued credentials to thousands of people, while others were using credentials in a business-to-business context where the volume of credentials was low but the value per credential was high. Thus the total value created by SSI is only loosely correlated with the sheer number of verifiable credentials in production. I’m always open to adopting better metrics to measure the value of SSI.